hexbyte
Startup program
Startup program
We architect and build high-performance applications using a modern, battle-tested technology stack.
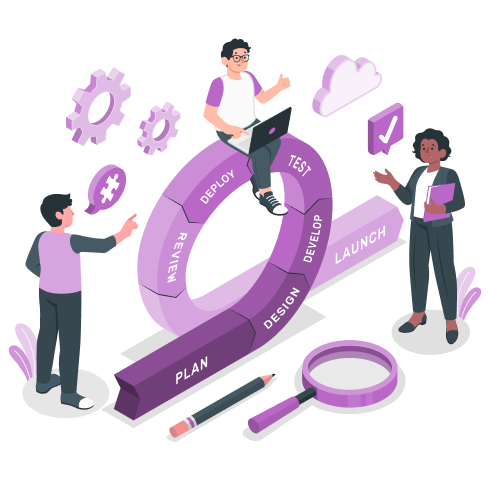
A transparent and collaborative journey from concept to launch.
Collaborative workshops to define project scope, goals, and user personas, ensuring a solid foundation.
Crafting intuitive and visually stunning user interfaces in Figma, focusing on user experience and flow.
Building seamless native and cross-platform apps with a focus on user engagement and optimized performance.
Implementing robust, scalable APIs to connect your app with essential third-party services and business logic.
Designing efficient and secure database schemas to handle your application's data with integrity and speed.
After rigorous testing, we deploy your application to a scalable cloud infrastructure with top-tier security measures.
Most versatile and rigorous developement process
Vulnerability scanning, real-time CVE detection, and code dependency monitoring.
WAF, DDoS protection, and enhanced network security.
Real-time secret detection in the codebase to prevent accidental sensitive data leaks.
Continuous assessment of code quality.
Protecting codes from malicious or vulnerable dependencies.
Scanning for vulnerabilities in containerized environments.